
by Christine Betterton-Jones, long-term JCC member and knowledge junkie
Security
First we need to know: How big is the problem? Am I at risk of being hacked?
When I started researching for this talk, I decided to Google the real scale of the problem for individual Internet users, rather than businesses , and came across this article in Scientific American: “Don’t feel guilty about your Online security habits – Most of the finger-wagging advice you hear is based on little or no evidence”
https://www.scientificamerican.com/article/dont-feel-guilty-about-your-online-security-habits/
Here are a couple of interesting quotes from this article:
“You might presume that there is a large body of evidence showing that if you do what you’re told—use strong passwords, run your antivirus software—you’ll significantly reduce your risk of cybercrime. Unfortunately, you’d be wrong.”
“The main source of information about online scams and what to do about them is from security experts. However, recommendations offered by these experts turn out to be inconsistent”
Security experts cannot agree on the measures people needed to be safe. 41 experts asked to list their “top five” came up with a total of 118 unique pieces of advice.
Am I likely to be hacked?
We don’t know if you are likely to be hacked – there’s no information about the risks for individual Internet users. Estimates of cybercrime are based on the corporate situation, and many businesses and government agencies are susceptible because they are using old software.
We are used to medical advice being based on evidence, unfortunately, security advice is not based on evidence.
For example, we know from hospital data that the elderly are more likely to suffer serious Covid and die. In contrast there doesn’t seem to be any data showing that Internet users who choose stronger passwords do better than those with weak passwords.
In a similarly analogy, studies have shown that treating seriously ill Covid patients with anti inflammatories can reduce the severity of their disease, but we don’t know how effective Internet security measures are in protecting us against hackers.
The studies simply haven’t been done. There are dangers – but don’t get paranoid!

We are faced with a lot of hype from companies which want to sell us their security products and we really don’t know what our personal risk is. There’s obviously a lot of fear. Is there a lot to fear?
Years ago at the JCC we recommended various anti-virus programmes to members. These gradually morphed and grew into Security suites. These are software packages and apps which provide all kinds of services, not just antivirus, but firewalls, parental controls, VPN (Virtual Private Network); webcam protection; secure browsers for money transfers, ransomware shields, anti Phishing etc. and often cover all your devices, Android, Windows and Apple. You have to purchase an annual subscription to the package. e.g

- Norton360 €30 per year
- Kasperky: €35 per year
- Trend Micro Maximum security:€ 30
- Avast Ultimate: up to €85 per year
- McAfee Total Protection multi device €23
https://www.techradar.com/news/best-internet-security-suites
Do I need a Security suite at all?
Internet security suites can be useful, but they are packed with features you don’t necessarily need. All of them adversely affect the performance of your device. i.e. slows it down, because the programme is constantly snooping about to see if anything bad is going on.
Most people would be fine without one because these days a lot of security is built into Internet browsers, e-mail systems and the operating systems which run our devices such as Windows, iOS and Android.
https://www.howtogeek.com/137278/htg-explains-why-you-dont-need-a-full-internet-security-suite/
Security in Windows
All you really need in Windows are:
- its own antivirus (Windows defender) and its security features ( e.g. Firewall),
- the security (e.g. anti-phishing) built into your Internet Browser and e-mail
- a malware scanner like Malware Bytes just to make sure that Windows Defender hasn’t missed anything.
- and some common sense (this is the most difficult thing to find)
Side note on Phishing: This is the fraudulent attempt to obtain sensitive information such as usernames, passwords and credit card details by impersonating oneself as a trustworthy person.
It’s typically carried out through fake emails, instant messaging and text messaging (Smishing)
Phishing often directs users to enter personal information into a fake website which matches the look and feel of the legitimate site.
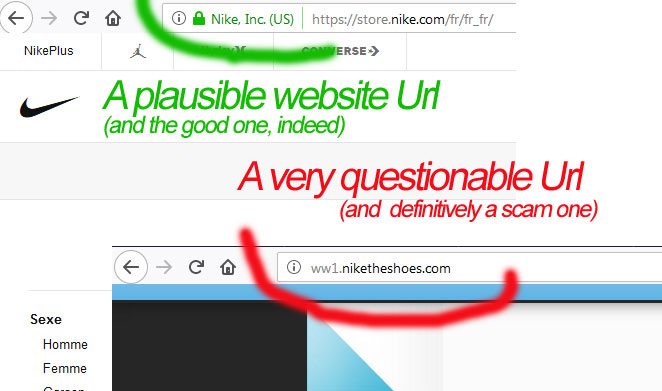
Spear Phishing is directed at specific individuals or companies. Attackers gather and use personal information about their target to increase their probability of success.
Guess what “Catphishing” is!

Windows will stop you from trying to go to a site if it thinks the site is malicious. Unfortunately some Government sites get mis-labelled as being dangerous!
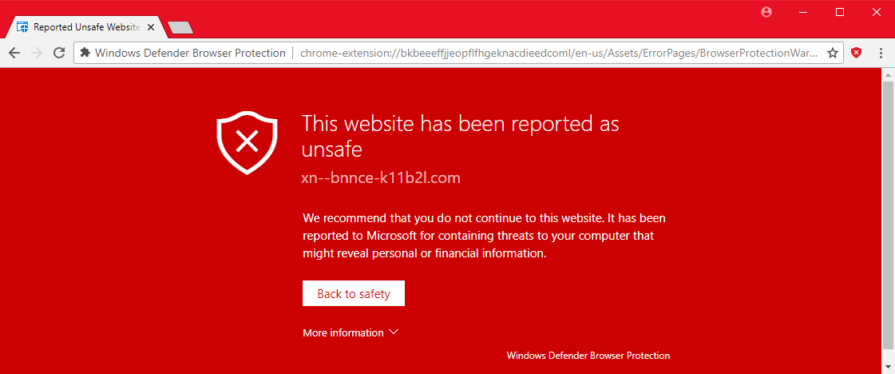
Tips for Windows users.
- Keep out of the dark and dingy parts of the Internet – if you poke around in the filth – expect to get dirty!
- Only install software from reputable sites – nevertheless Windows will warn you if it’s not sure about the software you are installing.
- Don’t click on dubious links in e-mails – however your e-mail provider will normally identify spam and has phishing protection. Your browser will also block phishing sites.
- Keep your Windows and browser up to date (stop running Windows 7 and 8!)
- Please ignore e-mails which ask you to invest money in some bank account to get a massive return and in turn asks for your debit card details – no software can protect against human gullibility and greed!
- Tell that bloke with a funny accent who rang you up saying he’s from Microsoft to go away.
Security in Apple (Ipad, iPhone, Mac)
You don’t need additional security features for Apple devices.
https://www.techadvisor.co.uk/feature/apple/do-you-need-antivirus-on-ipad-or-iphone-3669234/
Apple tightly controls the software which can be installed on its devices.
Also apple designed Apple Mac iOS so that each app runs in its own space, known as a sandbox.
The app can do what it likes (within reason) while in the sandbox, and it can even communicate with neighbouring apps, but it can’t leave the sandbox and interfere with other apps. This restriction leaves viruses, which usually spread and infect an entire device, with nowhere to go.
Security in Android
Android Antivirus Apps Are Useless. In the most recent report from AV-Comparatives (2020), we learned that most of the antivirus apps on Android don’t do anything to check apps for malicious behaviour. They just use on-line white/blacklists to flag apps as being safe or not safe, which is ineffective. Hence they are little more than advertising platforms with some fake buttons. They can get away with it because true Android viruses that take over your device are not as common as you’d expect.
Tips for Android users:
Download your apps from the Playstore and you should be fine. Malicious Apps are sometimes found there, but Google quickly removes them, and you’d be unlucky to pick up an infected one. However, mess about with other APK installations at your own risk – In so-doing you may be giving permission for malware to be installed on your phone.
Security Summary:
- These days, sophisticated cyber attacks are made against governments and large corporations.
- The average silver surfer is well protected by the security built into the software we use every day.
- The bad guys are probably looking for bigger Phish to catch.
- Beware of tricksters who try to trick you into revealing passwords and bank details.
Here’s a question to think about: Has anyone you know had their e-mail account compromised or their Bank account details stolen in recent years? – if so, what did they do to allow this to happen?
Privacy
In this digital age, no-one is completely private if they use the Internet. For example, Google analyses your e-mails for advertising purposes and even if you don’t use social media, perhaps you are a committee member of an association which has a web site or were tagged in a photo in the press? You have a digital footprint! (Try Googling some of the JCC Committee members and see what you can find. Google: person’s name Javea Computer Club)
Our concerns about privacy and security overlap – hence there’s a fear of cookies among some JCC members and they don’t want Google knowing everything about them. Should they be afraid?
What is a “Cookie”?
It’s a small piece of text data stored on the user’s computer by the web browser while you are visiting a website. Cookies enable a website (such as an on-line shop) to remember information such as items added to the shopping basket, things you have looked at, preferred language to use.
They are essential to the modern web. Authentication cookies tell the web site if you are logged in or not, and which account you are logged in with. If you delete cookies, they have to be saved anew when you next visit the site.
Third-party cookies are created by websites other than the one you are currently visiting. They are used for tracking your activity and on-line advertising.
https://clearcode.cc/blog/difference-between-first-party-third-party-cookies
The cost of free is your privacy.
This is naturally concerning, and an intrusion on our privacy. But Google and the like make money by advertising and advertising companies use cookies to build a profile of you from your browsing habits, so that they can target appropriate adverts at you.
European law (General Data Protection Regulation – GDPR) now insists that they can’t store third party cookies on your device without your consent. Hence we see all these new pop-ups which ask for you to agree to all (or some) of the cookies before you visit a site.
Some browsers can block this type of cookie. However, cookies are not a security threat. They are just are a small intrusion on our privacy.
I want to browse anonymously!
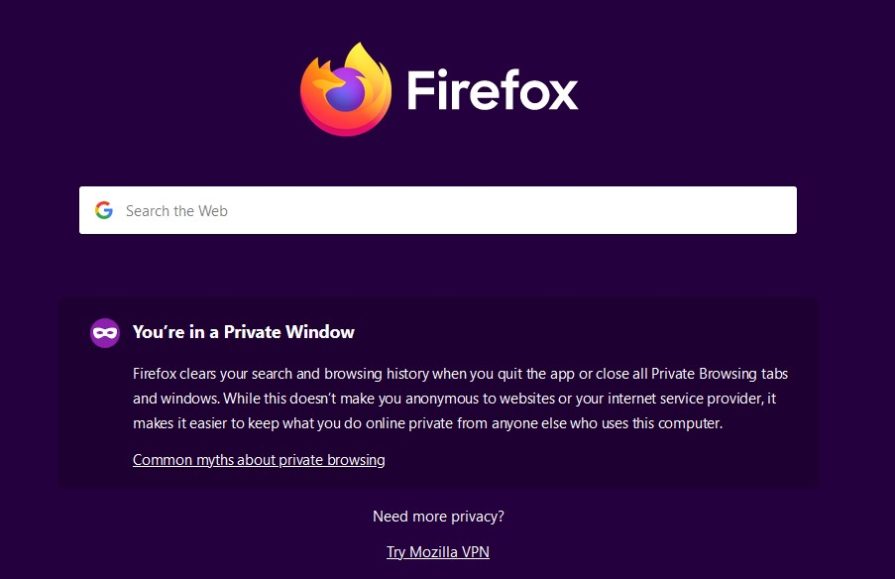
Some people worry that their Internet Service Provider, Internet search engines (like Google and Bing) and browsers (Edge, Chrome, Safari etc) can track where they have been poking around on the Internet … So all browsers enable you to browse “anonymously”:
- Incognito mode (Chrome and Safari) (Guest Mode for Google Assistant)
- InPrivate for Edge
- Private Window/ Private Browsing in Firefox Private Window in Vivaldi

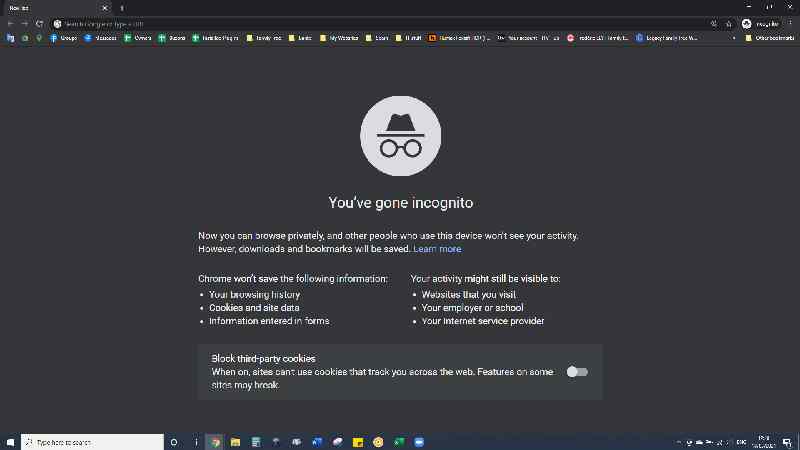
However: Incognito mode simply prevents your browsing history from being saved on your device and in your personal Google account. This includes searches, sites visited and cookies (though downloads and bookmarked sites will still show up). Basically, if others have access to your device or account, they won’t be able to see what you did while in Incognito mode.
These modes do not make you anonymous or hide your personal information when you log into websites,
Nor do they prevent Google, your internet provider, employers, advertisers or anyone else from seeing or collecting data about what you’re up to. This is all clearly stated when you open a new incognito tab.
What else can I do to be invisible!
Don’t use Google or Bing Search, use an alternative which does not track you e.g.:
- Startpage:
https://en.wikipedia.org/wiki/Startpage.com
This allows users to obtain Google Search results while protecting users’ privacy by not storing personal information or search data and removing all trackers. Startpage.com also includes an Anonymous View browsing feature that allows users the option to open search results via proxy for increased anonymity.
Startpage pays Google for the searches. It makes money by providing contextual advertising based on the keyword used to perform a search.
- DuckduckGo:
https://en.wikipedia.org/wiki/DuckDuckGo
This uses a “compilation” of over 400 sources to do searches, so it may not be as comprehensive as Startpage.
Use a Browser designed for privacy e.g.
- Firefox
https://www.mozilla.org/en-US/firefox/privacy/products/ - Tor, Brave, Iridium, GNU IceCat
hostingdata.co.uk/best-secure-browser - Vivaldi
https://www.cloudwards.net/vivaldi-review/


Everyone says I should have a VPN (Virtual Private Network)!
Virtual Private Networks route your internet connection via one of their servers and display an entirely different IP address (the number which identifies your device and geographical location) to the websites and other online services you interact with. Connections are encrypted and VPN servers can be in different countries.
However, VPNs do not make you anonymous. As soon as you send an e-mail or log into Facebook you’ll be leaving digital clues as to who you are, though you might be more private.
https://www.techadvisor.co.uk/feature/vpn/does-vpn-make-you-anonymous-3799104/
They are used for unlocking geoblocked services, such as BBCiPlayer, Netflix and Amazon Prime which have different content for different parts of the world and for people in oppressed countries to access sites which might be blocked by their governments.
They are also used by people who use torrent sites (which often contain material which infringes copyright) and are afraid that their Internet Service provider may block these sites or throttle back their Internet speed.
Privacy Summary:
- There are 7.9 billion people in the world today. Our value on the Internet lies in the fact that we are a market for those who want to sell us stuff.
- “Free” services on the Internet are paid for by advertising.
- Big Brother only bothers to watch you if you are up to no good. Tip: On social media, behave as you would behave in the village square.
